
© 2026 | All Right Revered.
Understand how containers play a part in cloud computing, see how they operate in the cloud, and figure out solutions for common challenges.

Chief Technology Officer | Data Science | Scale Up
A tech builder, mastering engineering processes and venture building by creating rapid, scalable, and solid product solutions. A staunch advocate for the disruptive capabilities of AI Co-Pilots in the software service industry.

In the landscape of cloud computing, containers emerge as a prevalent choice for the deployment and administration of software. Their primary function lies in abstracting applications from their underlying physical environment. Essentially, a container encapsulates all the dependencies associated with a software component and operates it within an isolated environment.
The deployment uniformity facilitated by containers, often utilizing the Docker container engine, extends across diverse environments—be it a public cloud, a private cloud, or a bare metal machine. Leveraging containers renders applications more adaptable to migration into the cloud computing environment.
Furthermore, the intrinsic characteristics of containers simplify the exploitation of the cloud’s extensive automation capabilities. Through the APIs provided by the container engine or orchestrator, these applications can effortlessly undergo deployment, cloning, or modification within the cloud computing domain.
The prevalence of containers is notably escalating within cloud environments, emerging as a viable alternative to the conventionally favored virtual machines (VMs) for large-scale enterprise workloads.
Containers prove particularly fitting for the following use cases in cloud computing environments:

Containers, characterized by their lightweight nature, align seamlessly with applications employing microservice architectures. This is especially relevant for applications consisting of numerous loosely connected and independently deployable services within a cloud computing architecture.
In DevOps, containers are really important. DevOps teams often use microservices for making applications, and they use containers to put these services into action. Containers are also helpful in setting up and adjusting the infrastructure, including tools for Continuous Integration and continuous deployment (CI/CD) within the cloud computing pipeline.
For organizations navigating multiple cloud environments, containers offer a valuable solution for workload migration between cloud computing environments. Serving as standardized units, containers facilitate flexible movement between on-premise data centers and any public cloud.
A prevalent approach to modernizing legacy applications involves containerization, allowing for a straightforward transition to the cloud computing domain-a strategy commonly referred to as “lift and shift.”
The roots of container technology trace back to the segmentation of partitions and the introduction of chroot processes within Linux. In contemporary settings, container engines manifest in the forms of application containerization, exemplified by Docker, and system containerization, as seen in Linux containers.
Operationally, at the kernel level of the operating system, containers leverage isolation to facilitate the deployment and execution of applications. Unlike traditional setups requiring a full operating system, containers operate by running only the essential files, libraries, and configurations needed to execute specific workloads. The host operating system serves as a regulator, constraining a container’s access to physical resources.
Within the realm of cloud computing, a prevalent approach involves using containers to execute instances of applications. Whether it’s an individual microservice or a backend application like a database or middleware component, containers enable the simultaneous operation of multiple applications on a shared cloud virtual machine (VM).
This ensures that issues with one container remain confined, preventing any adverse impact on other containers or the entire VM.
Cloud service providers extend various container-related services to users:
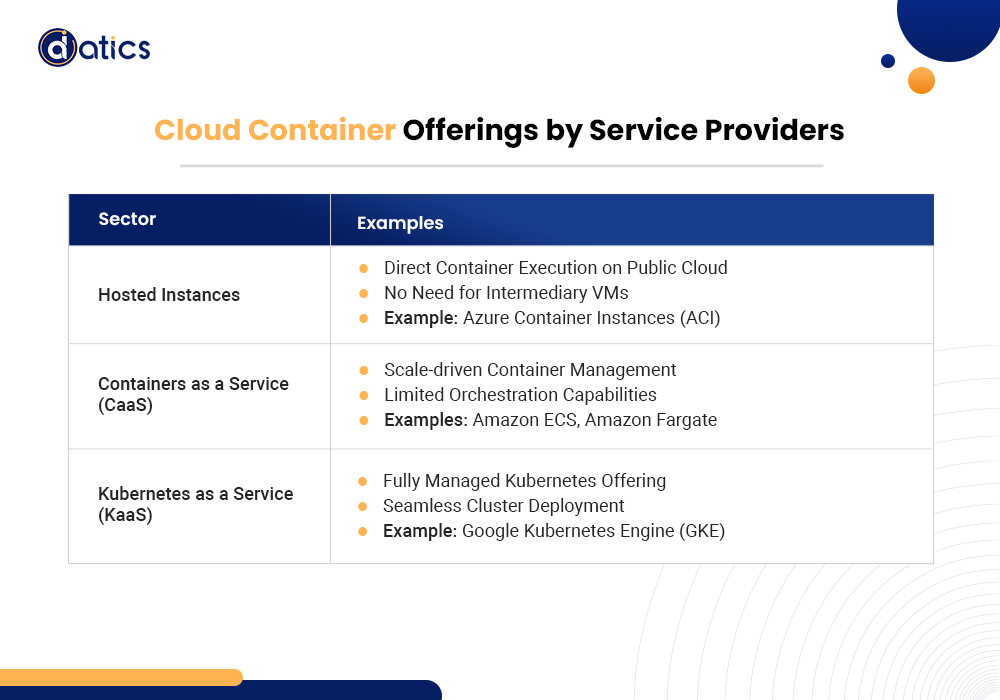
These services enable the direct execution of containers on public cloud infrastructure, eliminating the need for an intermediary cloud VM. Notable examples include Azure Container Instances (ACI).
If the answer to the above question is yes, then Datics AI could be your knight in shining armor. Our team of experts can help you build hyper-personalized chatbots (and more).
So what are you waiting for? Don’t waste any more time and get in touch with us now!
Designed for managing containers at scale, CaaS platforms typically offer limited orchestration capabilities. Examples include Amazon Elastic Container Service (ECS) and Amazon Fargate.
Imagine Kubernetes as a helpful assistant, known as Kubernetes as a Service (KaaS), taking care of all the complex stuff for you. It’s a popular tool that helps manage containers. Using KaaS, you can effortlessly create sets of containers on public cloud platforms, just like how Google Kubernetes Engine (GKE) does it.
Within the realm of cloud computing, the fundamental building block for deploying workloads is commonly a virtual machine (VM). Similar to containers, virtual machines represent independent computing environments abstracted from the underlying hardware. Unlike containers, however, VMs necessitate a complete operating system for execution.
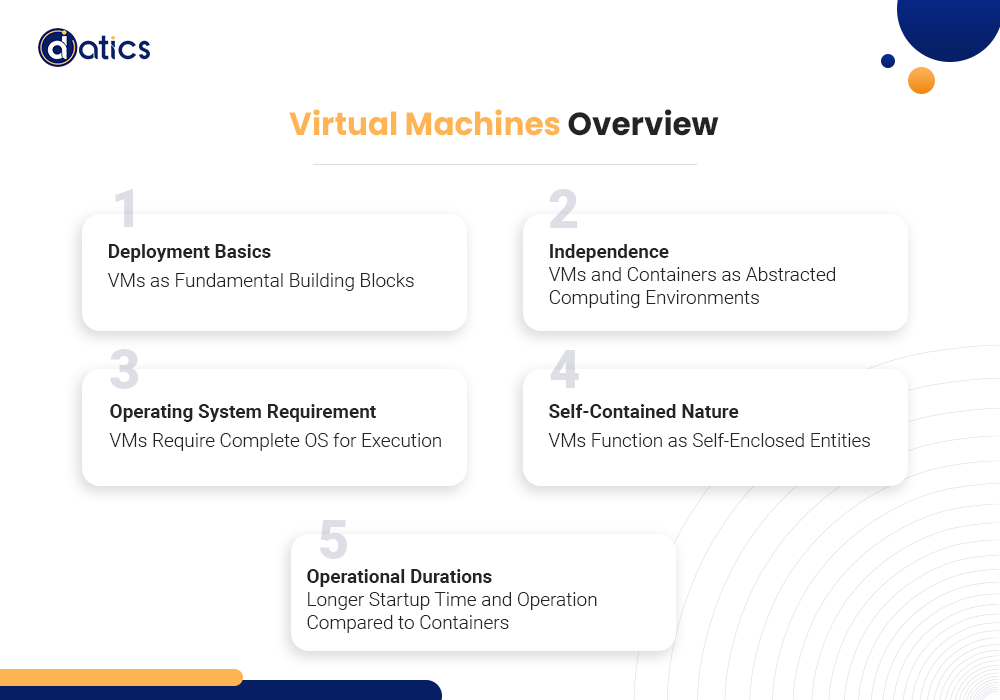
The versatility of VMs extends to running guest operating systems that differ from the host system. For instance, if the host system operates on Windows, a VM can seamlessly run Linux or any other operating system. In various technical scenarios, VMs offer enhanced isolation and security when compared to containers.
Yet, it’s crucial to note that a VM functions as a self-contained entity with a dedicated operating system. Consequently, it incurs a longer startup time and operational duration compared to a container. The images used to create new VMs, known as VM images, carry more weight than their container counterparts, making them less straightforward to automate.
In the cloud landscape, the prevalent practice involves running containers atop compute instances, which are essentially virtual machines in a technical sense. Notably, cloud service providers are now introducing the option to directly run containers on their bare metal servers without the need for VM intermediaries, following a model aptly termed “container instances.”
Following are the challenges you’d typically come across:
Containers present an opportunity for substantial cost reduction, but transitioning existing applications to this technology can pose difficulties in traditional computing setups. Many IT staff in organizations lack experience with containers, necessitating training or consultation support. The adoption of cloud computing, in itself, introduces technical hurdles for numerous operations teams, and the integration of containers may further complicate matters.

To address these challenges, organizations and technical teams must adapt to cloud-native technology. The container ecosystem provides a range of tools, including managed services designed for swift onboarding and user-friendly experiences, facilitating a smoother adoption process.
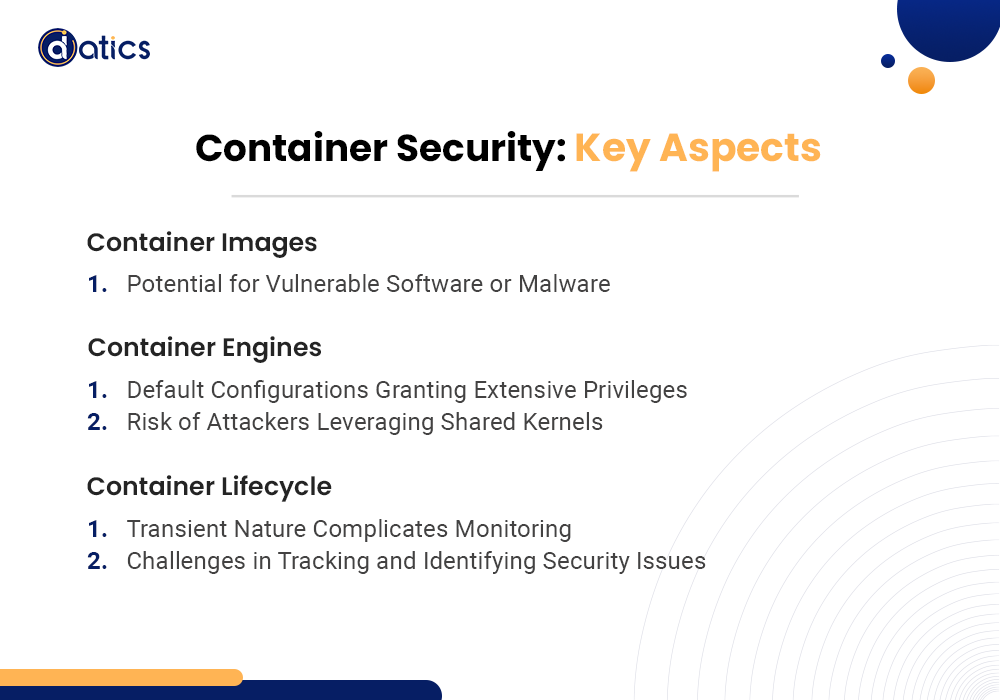
In the realm of container security within the cloud, a shared responsibility model prevails. The cloud provider assumes the responsibility of securing the underlying infrastructure, while customers are tasked with configuring security controls to safeguard their workloads and data. For containers, this entails your organization securing the containers themselves and the persistent storage volumes they utilize. Key security aspects include:
These may harbor vulnerable software components or malware.
Default configurations, as seen in engines like Docker, grant extensive privileges, posing a risk of attackers leveraging shared kernels to infect other containers and the host operating system.
The transient nature of containers complicates monitoring, tracking, and identification of security issues.
Security measures throughout the container lifecycle are vital. Conduct image scans to ensure safety, implement configuration best practices to secure and restrict privileges, and employ monitoring and security tools that cater specifically to containerized environments.
Container networks introduce a level of complexity that, if not managed effectively, can result in security issues. Traditional networking techniques are not applicable in containerized environments. Instead, Container Network Interface (CNI) standards and overlay networks are employed to create isolated, private networks for communication between containers and hosts.
The cloud environment adds another layer of complexity, with providers using specific networking terminology like virtual private clouds (VPC) and security groups. Managing networking for standalone containers on the cloud demands synchronization with established private networks. Mismanagement can lead to the unintended exposure of containers to the public Internet.
Many organizations mitigate these concerns by opting for managed container services or embracing orchestrators such as Kubernetes or Nomad. These orchestrators come equipped with built-in networking management tailored for clusters of containers, streamlining the intricate networking landscape.
In conclusion, the dynamic synergy between containers and cloud computing revolutionizes how businesses operate in the digital landscape. Overcoming challenges such as migration complexities, security concerns, and intricate networking, organizations now stand on the precipice of innovation. As a forward-thinking entity, embracing cloud-native technology becomes pivotal.
At Datics AI, we recognize the transformative power of containers and cloud computing. Our cloud services seamlessly integrate these technologies, offering a scalable and secure environment for your applications. Experience the ease of migration, fortified security protocols, and simplified networking management with our tailored solutions. Elevate your business to new heights with Datics AI as your trusted partner in the ever-evolving world of cloud computing. Unleash the full potential of your applications while we handle the intricacies, ensuring a future-ready, efficient, and resilient infrastructure for your success.
Share the details of your project – like scope, timeframe, or business challenges. Our team will carefully review them and get back to you with the next steps!

© 2026 | All Right Revered.
This guide is your roadmap to success! We’ll walk you, step-by-step, through the process of transforming your vision into a project with a clear purpose, target audience, and winning features.