
© 2024 | All Right Revered.
Worried about data breaches and unauthorized access lurking in your serverless environment? You’re not alone.

Cloud DevOps Engineer | LinkedIn Top Voice | Multi-Cloud Certified
An ambitious Cloud Engineer with a passion for cloud technologies and DevOps, proficient in designing and deploying cloud infrastructure and applications.

Serverless architecture offers exceptional scalability and cost-efficiency, it has completely changed the way we develop and implement applications. But this flexibility also raises new security risks.
It is now more important than ever to safeguard private information, stop illegal access, and maintain the integrity of your serverless environment. We will go into the domain of serverless security in this blog, covering subjects like patch administration, monitoring, logging, data encryption, and more.
Regardless of your level of experience with serverless architecture, this tutorial will provide you with the skills and resources you need to secure your serverless applications like a pro!
The term serverless is all the craze in the tech industry. It’s a different approach for developing applications without the requirement for server management. This allows developers to concentrate on writing code, and the infrastructure being managed by the cloud provider.
The benefits of serverless are the reasons that are driving its growth. Because you only pay for what you use, it’s economical. Moreover, it can withstand a sharp spike in traffic, it is scalable. It’s also efficient because it cuts down on the time needed for server maintenance.

However, enormous power also demands considerable responsibility. The possibility of data breaches, illegal access, and other security risks increases as more businesses use serverless. Data is the new money in today’s connected world, thus protecting your serverless environment is crucial. You’re at risk of disclosing private information and risking the integrity of your application if you don’t have enough security measures. Strong security benchmarks are required in this situation.
The goal of serverless security is to safeguard your data and code. It consists of operations like encrypting private information, keeping an eye out for suspicious activities, and routinely patching flaws in your code. Strong security precautions are becoming more and more necessary as serverless computing grows. It’s not just about building applications, but building them securely.
It’s crucial to make sure that your serverless apps are built with security in mind from the beginning in addition to these precautions. To protect against known vulnerabilities, this involves using secure libraries and APIs and sticking to recommended practices for secure coding. Last but not least, you may significantly reduce the danger of security breaches by training your staff on the value of security and giving them the required training.
Certain security issues with serverless architecture differ significantly from those with conventional server-based configurations. The dispersed nature of serverless apps is one of the main obstacles. Your code is distributed across several tiny, independent functions, each with a distinct operation, when you use a serverless architecture.
Scalability and agility are made possible by this, but it is also important to implement security precautions at every function level. The dependence on third-party providers and services is another difficulty. You frequently rely on different services offered by cloud providers for things like storage, authorization, and authentication when working in a serverless environment.
While these services are typically secured, however any misconfiguration or vulnerability in the code you write can expose your application to attacks.
Additionally, the dynamic nature of serverless applications presents security concerns. With servers being provisioned and deprovisioned automatically, it becomes critical to ensure that data and credentials are properly protected throughout the entire lifecycle.

In addition, a security risk may arise from the growing usage of APIs in serverless systems. Connecting various services and functions is a common usage for APIs, which, if not properly secured, can provide attackers access. Thus, it’s compulsory to have robust API security measures in place, such as restricting the amount of API calls that may be done in a certain amount of time and utilizing secure tokens for authentication.
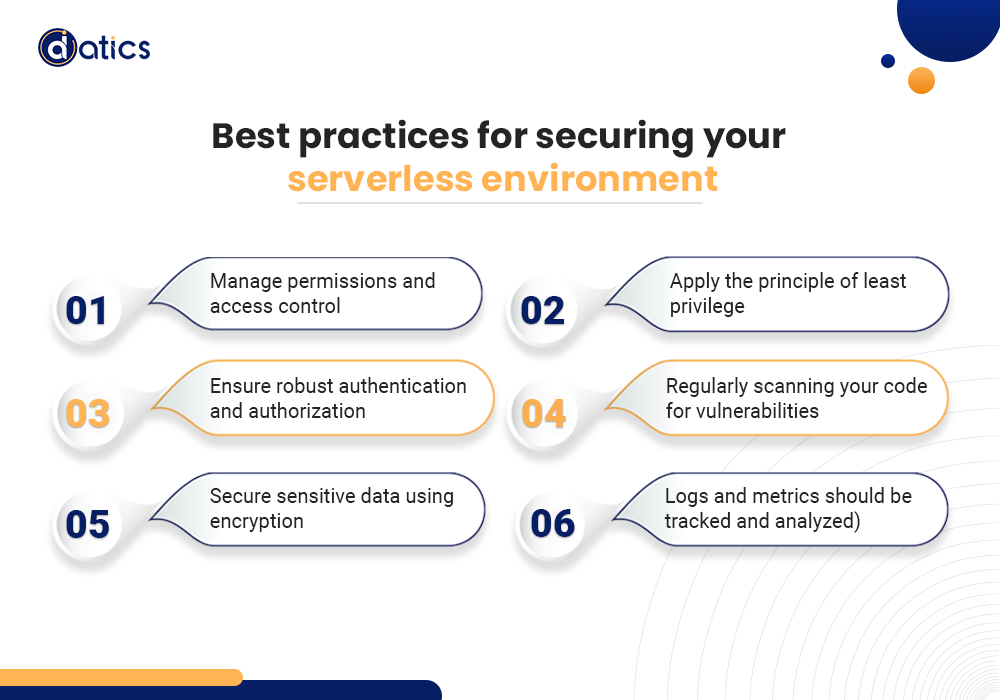
Now that we know exactly what unique security problems serverless architecture offers, let’s explore some recommended procedures for protecting your serverless environment.
Make use of the fine-grained access control features that your cloud provider offers. Limit the service access to only the resources that are required by using Identity and Access Management (IAM) roles to grant the right permissions.
Stick to the rule of giving each service the minimal amount of access that is required. By doing this, you can lessen the effects of any possible security breaches and stop unwanted access.
To guarantee that only authorized users can access your serverless applications, utilize strong authentication techniques like multi-factor authentication. Utilize access control systems to verify user authorization and stop illegal activity.
Your serverless apps may have security flaws that can be found and fixed with the assistance of automated security tools. These tools examine your code for common vulnerabilities and provide suggestions on how to fix them.
To prevent unwanted access, encrypt data while it’s in transit and at rest. With encryption, you can be sure that even if your data is stolen, it cannot be decoded without the encryption keys. This is especially crucial when handling sensitive information that could be compromised and has serious repercussions, such as financial data or personally identifiable information (PII).
Your serverless apps may have security flaws that can be found and fixed with the assistance of automated security tools. These tools examine your code for common vulnerabilities and provide suggestions on how to fix them.
Implement efficient monitoring and logging systems. They assist in identifying deviant behaviour that might indicate unauthorized access. A solid monitoring system maintains the security and performance of your app. If there’s a security concern, it can promptly notify you so you can address it. Logging captures the activity within your application. Logs can assist you in determining what went wrong and how to resolve a security breach.
Finally, it is critical to have a robust incident response plan in place. This strategy should specify what should be done in the event of a security breach, such as locating the breach, reducing damage, and alerting the appropriate parties. You can improve your serverless architecture’s security and protect your apps from danger by adhering to these recommended practices.
Serverless architectures are susceptible to vulnerabilities since they depend on a variety of external services and components. You may manage known security flaws and reduce potential dangers by updating your serverless setup regularly. Keep up with the most recent security upgrades for the frameworks and serverless platforms you use, as well as any third-party dependencies you employ.
Establish a clear update and patch management procedure to guarantee the security of your serverless architecture. Keep an eye out for vendor security alerts and patches, and implement them into your environment as soon as possible. Remember that keeping up with security upgrades is a continuous duty.

You must teach your team about serverless security best practices. Regular workshops and training sessions can improve your team’s understanding of the certain security issues that serverless approaches provide. From the fundamentals of serverless computing to more complex subjects like secure coding techniques and vulnerability management, these discussions cover a wide range of subjects.
Establishing a culture of security within your company is also crucial. This involves integrating security concerns into your development processes and promoting open conversations around security-related matters. Online forums and websites can offer insightful commentary and helpful guidance on serverless security.
This leads us to the conclusion that keeping your serverless environment safe and secure is essential for guarding your apps and data. It’s essential to carry out routine security audits and assessments in addition to these steps. These audits can assist in locating any possible vulnerabilities in your serverless setup and offer guidance on how to fix them.
Furthermore, understand that security considerations are not last-minute decisions but are required right from the design phase by implementing DevSecOps, a methodology that integrates security into your development lifecycle.
Last but not least, think about utilizing the knowledge of security experts or consulting services, who may offer insightful advice and suggestions based on the most recent security trends and serverless architecture best practices. Put your confidence in a serverless architecture that is well-secured, and reap the rewards for your data and applications.
Fortify Your Serverless Defense!
Share the details of your project – like scope, timeframe, or business challenges. Our team will carefully review them and get back to you with the next steps!

© 2024 | All Right Revered.
This guide is your roadmap to success! We’ll walk you, step-by-step, through the process of transforming your vision into a project with a clear purpose, target audience, and winning features.